"Count Lawrence Snyder among those who believe that if the information security profession can be saved, women are its only hope.
Security Bytes
Wednesday, April 2, 2014
Women in cybersecurity: The time is now
Article from an interview I did with Eric Pariz, who is the executive editor of TechTarget's Media Security Group.
"Count Lawrence Snyder among those who believe that if the information security profession can be saved, women are its only hope.
Saved may be a strong word, but Snyder, department chair of the new cybersecurity studies program at Bay Path College, understands the stakes. The demand for qualified, experienced information security practitioners far outpaces the supply: The International Information Systems Security Certification Consortium estimates that last year about 332,000 InfoSec pros joined the global workforce of about 3.2 million, but the field needs as many as 2 million more practitioners, according to (ISC)2 Executive Director W. Hord Tipton." ........Women in cybersecurity: The time is now
"Count Lawrence Snyder among those who believe that if the information security profession can be saved, women are its only hope.
Sunday, March 23, 2014
Mac and iOS Show Thier Vulnerabilities.......
About a month ago Apple released security updates
for Mac operating systems, as
well as a security update for the iPhone and iPad. For many observers, particularly the media, this was an extraordinary
event, as there is a perception of invulnerability as it relates to Mac and
other Apple products. Unfortunately this
is more myth than fact. The reality is
that today there is exists malware that is specifically designed to target and
exploit weaknesses with Mac platforms. This
can easily be explained by examining market penetration of the various
operating systems. Until recently the
majority of business in America utilized Windows based machines. There is an economic term that helps explain
this phenomenon, homo economicus. Homo economicus or economic human, is the
concept that humans as rational and self-interested creatures that look to
maximize utility as a consumer and profit as a producer. In other words, humans, in this case cybercriminals
desire to make the most impact with the lowest cost. Cybercriminals
recognize that Windows dominate the personal and business computer market, so by targeting the Windows OS they will get the
“biggest bang for their buck” .
Recent
surveys of American business indicate that Mac’s are more popular than ever, so
one can expect that there will be an increase in the volume of malware attacks
specifically targeting Mac OS’s.
Unfortunately, culturally the myth of Macs invulnerability to malware
still exists and it can lead to some serious security concerns for
organizations and user.
Symantec recently completed a study of Mac machines
that were infected with malware and found that only 2.5 percent of threats
found on Macs are Mac malware. The
remaining malware was Windows malware.
Mac users were being tricked into downloading malware, the good news is
that 97.5 percent of the time the malware would not impact the Mac machine. The
bad news is that if the Mac was connected to a shared drive, or transferred the
malware to a USB which was then inserted or shared with a Windows machine then
that Windows machine is a potential victim.
Clearly there is a significant fewer number of
malware attacks directed at Mac than Windows.
For a historical context, ELK Cloner was the first self-propagating
piece of malware was designed to attack the Apple II in 1982. The first piece of malware targeting Mac was
in 1987 called nVIR. More of an annoyance
than destructive, they both were designed to spread via contaminated floppy
disks. Over time the Mac OS operating
system was hardened and the ability to introduce malware on the system was more
difficult. Malware writers began to rely
on social engineering and Trojans to trick users into installing the
malware. More recently, in 2012 one Mac
threat (Flashback) infected approximately 600,000 machines, or about 1 out of
every 100 Macs worldwide. It targeted a java vulnerability to gain access to
the machines that visited an infected website. The bad news is that Mac users seem to be as
susceptible to downloading malware as a pc user. By perpetuating the myth that Macs are not as
susceptible to malware as pc machines seems to lead to as risky or perhaps
riskier behavior for the Mac user.
Apple has recognized that there is an increased
threat level directed at their OS and did respond with XProtect for the Snow
Leopard OS. XProtect would proactively
identify malware during the download process and notify the user, giving them
the option of cancelling the download or moving it to trash. It was a
definition based malware that is designed to work just like traditional
antivirus software. Unfortunately, Apple
is somewhat secretive about how it works.
There is limited information on the Apple website about how it works,
when it is being updated or what it is being updated with.
More recently Apple released GateKeeper, in the
Mountain Lion OS. GateKeeper, is a
behavioral based protection tool that asks the user various questions about
their downloading behavior, where the use downloads from. Depending on where the user indicates where
they download from will dictate the security notifications they receive and the
guidance GateKeeper provides.
Unfortunately these developments have not deterred malware
writers from targeting Mac OS. The 2013
Internet Security Threat Report, Volume 18 found the following:
- 42% increase in targeted attacks in 2012.
- 31% of all targeted attacks aimed at businesses with less than 250 employees.
- One waterhole attack infected 500 organizations in a single day.
- 14 zero-day vulnerabilities.
- 32% of all mobile threats steal information.
- A single threat infected 600,000 Macs in 2012.
- Spam volume continued to decrease, with 69% of all email being spam.
- The number of phishing sites spoofing social networking sites increased 125%.
- Web-based attacks increased 30%.
- 5,291 new vulnerabilities discovered in 2012, 415 of them on mobile operating systems.
Assuming that Mac OS and IOS
continues to gain market share in both personal and business use, we can expect
there to be continued interest on the part of malware writers and
cybercriminals in targeting the various OS.
Organizations that are adopting the Mac OS will struggle to provide
adequate security controls over the OS for two reasons, the misconceptions of the users, and the lack of developer information relating to security controls of the OS.
In today’s cyber environment, organizations must make security decisions based on meaningful risk analysis and threat matrixes. In order for Mac and iOS to be adopted by more organizations there must be an increase in transparency on what Apple is doing to protect their various operating systems from these threats. I would expect that organizations would demand more information from Apple on how they are protecting against malware and targeted threats directed at the Mac and IOS operating systems, as a means to protect their networks, before we see wide spread integration into the business environment.
In today’s cyber environment, organizations must make security decisions based on meaningful risk analysis and threat matrixes. In order for Mac and iOS to be adopted by more organizations there must be an increase in transparency on what Apple is doing to protect their various operating systems from these threats. I would expect that organizations would demand more information from Apple on how they are protecting against malware and targeted threats directed at the Mac and IOS operating systems, as a means to protect their networks, before we see wide spread integration into the business environment.
Tuesday, February 11, 2014
How Cybercriminals Turn Your Stolen Emails Into Cash; An Analysis Of Recent Data Breaches
On February 3, we learned of another retail data breach in what has been an extremely active cybersecurity season. The most recent incident involved a breach of White Lodging, a company that holds franchises on hotels such as Hilton, Marriott, Sheraton and Westin. Initial reports indicate the breach resulted in the disclosure of debit and credit card information of thousands of guests who made purchases in hotel restaurants and shops. According to information released by Marriott, there is no indication the computer system responsible for front desk operations was compromised. What is not clear is to what extent additional personally identifiable information (PII) was compromised as a result of this breach.
Over the past three months we have seen six major security breaches resulting in the release of hundreds of millions of debit and credit card accounts. Those breaches also resulted in the disclosure of as many, if not more, email addresses, telephone numbers, mailing addresses and other pieces of what is often considered lesser bits of information. Yet, because of the focus on financial fraud as the result of a data breach, there continues to exist a lack of understanding of the value of what is often considered innocuous pieces of information, such as email addresses. After all, it is easy to understand how a cybercriminal can turn stolen credit and debit card information into money, and the value of those accounts to the legitimate owners is clearly evident. The question is, what is the value of an email address to a cybercriminal? How can a cybercriminal convert a batch of stolen emails into money?
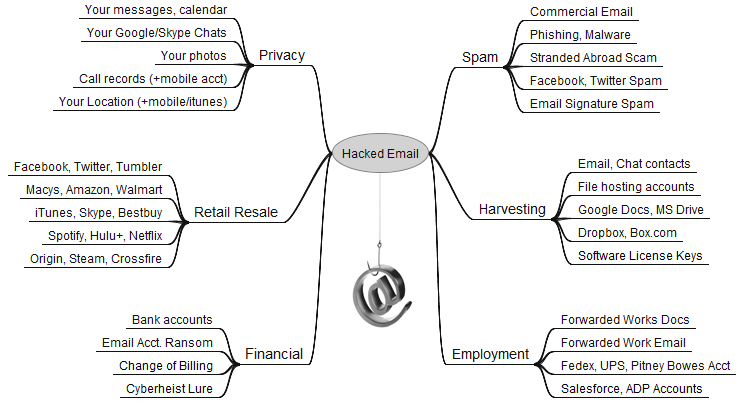
There is perhaps no other piece of personally identifiable information that is so integrated in our online persona as our email address. Whether you are registering for a Facebook account, an Amazon account, online banking or any other online service, you are generally required to provide an email address. The individual that has control over the email address, coupled with a weak or easily guessed password, could have control over multiple accounts attached to those email addresses. When you take a moment and aggregate all of the individual accounts and services tied to your email, it is easy to understand the value of your email account. Below is a representation of how ubiquitous an individual email account is to the average consumer.
Perhaps one of the most popular attacks targeting stolen email addresses is the phishing attack. A typical phishing attack comes in the form of
a bogus email purporting to be from a financial institution where the
recipient has an account. The message will inform the recipient that
there has been some sort of change at the bank – perhaps a new security
control or a change to the banking system – that requires the victim to
reconfirm their account information. Designed to create a sense of urgency on the part of the victim, the
email will include a web link where the victim will be prompted to
update his or her personal information. Unbeknownst to the victim, the
link will lead to a fake website, specifically designed to mirror the
legitimate bank website, where their personal information will be
captured by the cybercriminal.
Converting stolen emails to cash is purely a numbers game. Take, for instance, the Target breach; it is estimated that approximately 70 million emails were stolen during the breach (Step 1). If we assume for a moment that one person was in possession of those emails, we can quickly demonstrate how lucrative it is to steal email addresses.
Assuming that the cybercriminal utilized all 70 million emails in a phishing attack, perhaps offering them free credit monitoring, approximately 5%, or 3.5 million messages will make it through email filters and be presented to the recipient (Step 2). Of those 3.5 million emails, approximately 5%, or 175,000 recipients will click on the phishing link provided in the email (Step 3). Statistics show that approximately 2% of those individuals who clicked on the provided link will enter personal information such as social security numbers or date of birth into the phishing site (Step 4). On average, an individual experiences a loss of about $361.00 in a phishing scam (Step 5), when the cybercriminal utilizes their stolen information. The potential payout in this scenario results in the cybercriminal netting approximately $1.2 million, with a very low likelihood of detection.
It is important that we remember that when an organization experiences a data breach, the impact on the consumer is far reaching. While it is critical that victims of a breach monitor their financial accounts for abuses as a result of a breach, it is equally important that they take proactive steps to minimize their exposure for residual losses of personally identifiable information that may have been compromised. Understanding the ubiquity of key pieces of information you provide to third parties will help you protect yourself in the event your information is part of a data breach.
Over the past three months we have seen six major security breaches resulting in the release of hundreds of millions of debit and credit card accounts. Those breaches also resulted in the disclosure of as many, if not more, email addresses, telephone numbers, mailing addresses and other pieces of what is often considered lesser bits of information. Yet, because of the focus on financial fraud as the result of a data breach, there continues to exist a lack of understanding of the value of what is often considered innocuous pieces of information, such as email addresses. After all, it is easy to understand how a cybercriminal can turn stolen credit and debit card information into money, and the value of those accounts to the legitimate owners is clearly evident. The question is, what is the value of an email address to a cybercriminal? How can a cybercriminal convert a batch of stolen emails into money?
There is perhaps no other piece of personally identifiable information that is so integrated in our online persona as our email address. Whether you are registering for a Facebook account, an Amazon account, online banking or any other online service, you are generally required to provide an email address. The individual that has control over the email address, coupled with a weak or easily guessed password, could have control over multiple accounts attached to those email addresses. When you take a moment and aggregate all of the individual accounts and services tied to your email, it is easy to understand the value of your email account. Below is a representation of how ubiquitous an individual email account is to the average consumer.
 |
| Ref: krebsonsecurity.com |
Converting stolen emails to cash is purely a numbers game. Take, for instance, the Target breach; it is estimated that approximately 70 million emails were stolen during the breach (Step 1). If we assume for a moment that one person was in possession of those emails, we can quickly demonstrate how lucrative it is to steal email addresses.
Assuming that the cybercriminal utilized all 70 million emails in a phishing attack, perhaps offering them free credit monitoring, approximately 5%, or 3.5 million messages will make it through email filters and be presented to the recipient (Step 2). Of those 3.5 million emails, approximately 5%, or 175,000 recipients will click on the phishing link provided in the email (Step 3). Statistics show that approximately 2% of those individuals who clicked on the provided link will enter personal information such as social security numbers or date of birth into the phishing site (Step 4). On average, an individual experiences a loss of about $361.00 in a phishing scam (Step 5), when the cybercriminal utilizes their stolen information. The potential payout in this scenario results in the cybercriminal netting approximately $1.2 million, with a very low likelihood of detection.
It is important that we remember that when an organization experiences a data breach, the impact on the consumer is far reaching. While it is critical that victims of a breach monitor their financial accounts for abuses as a result of a breach, it is equally important that they take proactive steps to minimize their exposure for residual losses of personally identifiable information that may have been compromised. Understanding the ubiquity of key pieces of information you provide to third parties will help you protect yourself in the event your information is part of a data breach.
Thursday, January 30, 2014
Ransomware - Holding Your Data Hostage
Cryptolocker is a ransomware that was discovered in September 2013. It utilizes both technical and nontechnical methods to infect computers, identify critical files and render them unavailable until victims pay for their release.
The most common method for infection is through the use of phishing emails that encourage the recipient to click on a link that enables the malicious software to be downloaded, opened and executed. Once installed the malware seeks out user created files such as .doc, .xls, .pdf, and others. Using a robust encryption application the malware encrypts each of these files rendering them unavailable to anyone who does not have the key needed to decrypt, which happens to be stored on a remote server under the control of the cybercriminal. Cryptolocker is especially aggressive in that it has the ability to locate files the victim has access to on not only the local drive, but files located on shared network drives, USB drives, external hard drives, network file shares and in some cases even some cloud storage devices.
Individuals and organizations that find themselves falling victim to a ransomware infection such as Cryptolocker should contact your IT administrator and determine what your incident response plan is and start the remediation process.
Some common recommendations to follow if you believe that your computer has been infected include:
Due to the inability of most antivirus software applications to proactively detect the malicious software associated with ransomware, the most successful strategy is to prevent the infection of the malware.
One of the most important things an individual or an organization can do to limit their exposure is to ensure that individuals are aware of the threat and you do not open suspicious emails or unexpected attachments.When in doubt the recipient should verify the identity of the sender and the specific contents of any attachments.
Regular backup of all systems will limit the impact of data or system losses.
Organizations should restrict access to sensitive files and conduct regular review of user access to ensure that it is limited to only that level required to perform their work duties.
Regular updates of all antivirus programs and enabling automatic updates of your AV signatures and software as well as ensuring that your system is updated and patched in a timely manner will also help reduce your exposure.
Ransomware is an area that is going to be a real issue going forward as it can be very lucrative for the cybercriminal, and the risk of being caught is still relatively low. According to an article in PCWorld, the creator of the Cryptolocker virus may have made as much as $30 million in just 100 days;if that is the case, you can guarantee that more ransomware is on the way.
The most common method for infection is through the use of phishing emails that encourage the recipient to click on a link that enables the malicious software to be downloaded, opened and executed. Once installed the malware seeks out user created files such as .doc, .xls, .pdf, and others. Using a robust encryption application the malware encrypts each of these files rendering them unavailable to anyone who does not have the key needed to decrypt, which happens to be stored on a remote server under the control of the cybercriminal. Cryptolocker is especially aggressive in that it has the ability to locate files the victim has access to on not only the local drive, but files located on shared network drives, USB drives, external hard drives, network file shares and in some cases even some cloud storage devices.
Individuals and organizations that find themselves falling victim to a ransomware infection such as Cryptolocker should contact your IT administrator and determine what your incident response plan is and start the remediation process.
Some common recommendations to follow if you believe that your computer has been infected include:
- Immediately disconnect your system from the network. This will prevent the virus from further encrypting additional files on your network.
- Turn off any data synchronization software that automatically syncs your data to a central server.
- If you decide to restore your files from backup copies, once you have removed all remnants of the virus, including ensuring that your registry has been appropriately cleaned, it is essential that you identify and utilize a backup from a time period prior to the original virus infection.
Due to the inability of most antivirus software applications to proactively detect the malicious software associated with ransomware, the most successful strategy is to prevent the infection of the malware.
One of the most important things an individual or an organization can do to limit their exposure is to ensure that individuals are aware of the threat and you do not open suspicious emails or unexpected attachments.When in doubt the recipient should verify the identity of the sender and the specific contents of any attachments.
Regular backup of all systems will limit the impact of data or system losses.
Organizations should restrict access to sensitive files and conduct regular review of user access to ensure that it is limited to only that level required to perform their work duties.
Regular updates of all antivirus programs and enabling automatic updates of your AV signatures and software as well as ensuring that your system is updated and patched in a timely manner will also help reduce your exposure.
Ransomware is an area that is going to be a real issue going forward as it can be very lucrative for the cybercriminal, and the risk of being caught is still relatively low. According to an article in PCWorld, the creator of the Cryptolocker virus may have made as much as $30 million in just 100 days;if that is the case, you can guarantee that more ransomware is on the way.
Thursday, January 16, 2014
Perfect Security is Perfectly Impossible
I was recently listening to an analysis of the Target security breach on
NPR's On Point with Tom Ashbrook (On Point). One of his guests for the show was David
Lazarus who is a consumer columnist for The Los Angeles Times. Mr
Lazarus had written an article that took the position that companies are
willfully leaving customer information vulnerable to disclosure because the
cost of securing the data is too expensive (Lazarus, 2014).
Mr. Lazarus makes a valid point when he indicates that it is expensive to secure networks and data, and it is indeed a business decision to balance between security and usability or availability. Unfortunately, in my opinion, he jumps off the track when he suggests that organization can deploy a multitude of security mechanisms to provide absolute security.
As I am sure you are aware, every security technology has inherent vulnerabilities. Every tool that is introduced into a network can and with enough time will be defeated. In other words, there will never be perfect security in a network designed for commerce. Even encryption, which some tout at the holy grail for securing data, has vulnerabilities that allow for the possibility of its defeat.
It is true that businesses are collecting more and more information from its customers. Many are asking for email addresses, telephone numbers, and other non-financial information at the point of sale. Others are offering club cards, memberships and discounts which collect the same information. This information, while innocuous can be a rich target for hackers and identity thieves. What is often forgotten, or perhaps overlooked, is that none of this information is needed to complete the transaction. Customers can simply say no, refuse to provide their email, or telephone number, and simply complete the transactions. This might mean that you are not able to receive a discount on your purchase, or miss out on special sales, but your information will be just a little bit more secure.
I do support, as I have previously posted, the idea of assessing a fee to organizations that experience a breach, perhaps with a sliding scale if it can be determined that the organization was negligent in providing security for its customer data, but I would be caution of making the fine so high that it becomes a deterrent to reporting. I also feel that any fines collected due to a breach should be used to create a "super fund" to provide monetary support for consumers that have their information compromised as a result of a breach, provide funding for research and education and for the identification and prosecution of cybercriminals.
To me, the most unsettling fact about the recent string of breaches is the time that elapsed between the initial breach and the organizations public notification of the breach. There is no reason that an organization should be sitting on a known breach for four weeks, without providing notification to those that were affected. That to me is unconscionable and should be a primary concern for our legislature to address.
The bottom line is there is no such thing as personal security, consumers need to revalue their personal privacy and control how it is distributed, organizations need to voluntarily disclose data breaches in a more timely manner, and as a nation we do need to examine a comprehensive breach notification law.
Mr. Lazarus makes a valid point when he indicates that it is expensive to secure networks and data, and it is indeed a business decision to balance between security and usability or availability. Unfortunately, in my opinion, he jumps off the track when he suggests that organization can deploy a multitude of security mechanisms to provide absolute security.
As I am sure you are aware, every security technology has inherent vulnerabilities. Every tool that is introduced into a network can and with enough time will be defeated. In other words, there will never be perfect security in a network designed for commerce. Even encryption, which some tout at the holy grail for securing data, has vulnerabilities that allow for the possibility of its defeat.
It is true that businesses are collecting more and more information from its customers. Many are asking for email addresses, telephone numbers, and other non-financial information at the point of sale. Others are offering club cards, memberships and discounts which collect the same information. This information, while innocuous can be a rich target for hackers and identity thieves. What is often forgotten, or perhaps overlooked, is that none of this information is needed to complete the transaction. Customers can simply say no, refuse to provide their email, or telephone number, and simply complete the transactions. This might mean that you are not able to receive a discount on your purchase, or miss out on special sales, but your information will be just a little bit more secure.
I do support, as I have previously posted, the idea of assessing a fee to organizations that experience a breach, perhaps with a sliding scale if it can be determined that the organization was negligent in providing security for its customer data, but I would be caution of making the fine so high that it becomes a deterrent to reporting. I also feel that any fines collected due to a breach should be used to create a "super fund" to provide monetary support for consumers that have their information compromised as a result of a breach, provide funding for research and education and for the identification and prosecution of cybercriminals.
To me, the most unsettling fact about the recent string of breaches is the time that elapsed between the initial breach and the organizations public notification of the breach. There is no reason that an organization should be sitting on a known breach for four weeks, without providing notification to those that were affected. That to me is unconscionable and should be a primary concern for our legislature to address.
The bottom line is there is no such thing as personal security, consumers need to revalue their personal privacy and control how it is distributed, organizations need to voluntarily disclose data breaches in a more timely manner, and as a nation we do need to examine a comprehensive breach notification law.
Tuesday, January 14, 2014
40 Million? 70 Million? 110 million? We are still not sure how many customer data records have been compromised in the last 12 weeks
When initially reported by Target, it was estimated that
approximately 40 million credit and debit card
customer files had been compromised as a result of a data breach, which
occurred sometime between November 27 and December 15, 2013 (Wall Street Journal, Corporate Intelligence).
After initially being reported by the KrebsOnSecurity on the 18 of December,
Target makes a public acknowledgement of the breach on the 19th,
confirming that customer names, credit or debit card numbers, expiration dates
and encrypted security codes had be compromised. During the course of their investigation, in
conjunction with Department of Justice, the Secret Service and Verizon
Communication, on December 27th, Target discovers that encrypted
debit card PIN information was also compromised as a result of the breach. Two weeks later, on January 10, Target
announces that some additional 70 million customers had their personal
information stolen during the breach. This includes names, mailing addresses,
phone number, or emails (Wall Street Journal, Corporate Intelligence). On January 11, Neiman Marcus confirms that it
too was a victim of a data breach during the same time frame as Target and that
they were working with the U.S. Secret Service to investigate the break
in. Neiman Marcus also informs the
public that they were unable or unwilling to disclose the number of customer
records that were compromised. Today,
according to Reuters, there were at least three other smaller breaches on other
well-known U.S. retailers in a similar fashion as the Target and Neiman Marcus
breaches (Reuters).
Most states (46 out of 50)(National Conference of State Legislatures)
have laws that require companies to notify customers when personally identifiable
information is compromised, such as social security numbers. In Massachusetts, Mass General Law 93H-1 et
seq. states when a breach of security
results in the disclosure of a
resident’s first name and last name, or first initial and last name in combination
with any one or more of the follow data elements( social security number;
drivers license or state –issued identification card; or financial account information with or without required security codes)that
agency must notify the individual. Currently
there is no federal law requiring consumer notification as a result of a data
breach.
The reality of today is that data breaches happen and they
will continue to happen. As new security technologies are brought into the
marketplace, hackers and cybercriminals will continue to test the security
controls looking and exploiting weaknesses in the technology. Organizations will experience temporary
losses as consumers’ confidence waivers as a result of the breach notification,
but those profits are likely to return as the public generally has a short
memory and will eventually forget the incident.
This is short lived until the next round of breaches are discovered and
disclosed.
The real issue is the lack of accountability for organizations
to take meaningful steps to protect consumers, and make them whole. Currently the remedy for consumers caught up
in a data breach is credit monitoring services. While this is an important step
to take to protect consumer credit score, it is woefully inadequate in
protecting consumers from other forms of personally identifiable information abuse. Credit monitoring will not monitor public
record databases, driver license records, criminal records, social security
records, or medical records. There is nothing that compels organizations to
provide meaningful long term protection for victims of data breaches.
It has been floated as an idea that speaks to the need of a
federal law that penalizes organizations that are victims of a data breach who
do not inform consumers. Recognizing
that it is impossible to prevent every type of security issue, I find that
suggestion naïve and overly simplistic.
What I would suggest is a law that requires organizations to contribute
to a superfund, similar to those established to clean hazardous substances, a
monetary fee for each data record breached.
For instance, if organizations were required to submit $1 for each data
record compromised as a result of a data breach, Target would contribute
between $40 and $70 million dollars to the fund. A portion of the fund could be set aside for
future claims of repeat victimization of consumers who were initially
victimized in a breach. After all, once
your personal information is released, it may be years before the extent of the
compromise is personally quantified. The
fund could also be used to provide resources for research and education in the
field of computer security, allowing specifically for research and training in
the prevention, detection and mitigation of cyber threats. Finally, funding could be provided to offset
the cost of investigating, and prosecuting individuals responsible for the breach
and future crimes related to the misuse of disclosed information.
Subscribe to:
Posts (Atom)
