Over the past three months we have seen six major security breaches resulting in the release of hundreds of millions of debit and credit card accounts. Those breaches also resulted in the disclosure of as many, if not more, email addresses, telephone numbers, mailing addresses and other pieces of what is often considered lesser bits of information. Yet, because of the focus on financial fraud as the result of a data breach, there continues to exist a lack of understanding of the value of what is often considered innocuous pieces of information, such as email addresses. After all, it is easy to understand how a cybercriminal can turn stolen credit and debit card information into money, and the value of those accounts to the legitimate owners is clearly evident. The question is, what is the value of an email address to a cybercriminal? How can a cybercriminal convert a batch of stolen emails into money?
There is perhaps no other piece of personally identifiable information that is so integrated in our online persona as our email address. Whether you are registering for a Facebook account, an Amazon account, online banking or any other online service, you are generally required to provide an email address. The individual that has control over the email address, coupled with a weak or easily guessed password, could have control over multiple accounts attached to those email addresses. When you take a moment and aggregate all of the individual accounts and services tied to your email, it is easy to understand the value of your email account. Below is a representation of how ubiquitous an individual email account is to the average consumer.
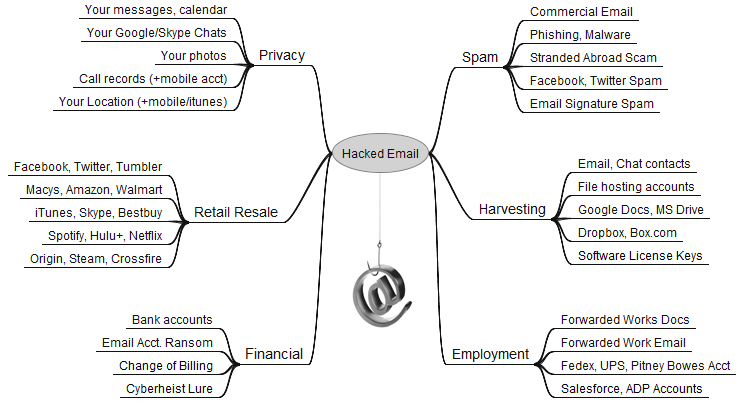 |
| Ref: krebsonsecurity.com |
Converting stolen emails to cash is purely a numbers game. Take, for instance, the Target breach; it is estimated that approximately 70 million emails were stolen during the breach (Step 1). If we assume for a moment that one person was in possession of those emails, we can quickly demonstrate how lucrative it is to steal email addresses.
Assuming that the cybercriminal utilized all 70 million emails in a phishing attack, perhaps offering them free credit monitoring, approximately 5%, or 3.5 million messages will make it through email filters and be presented to the recipient (Step 2). Of those 3.5 million emails, approximately 5%, or 175,000 recipients will click on the phishing link provided in the email (Step 3). Statistics show that approximately 2% of those individuals who clicked on the provided link will enter personal information such as social security numbers or date of birth into the phishing site (Step 4). On average, an individual experiences a loss of about $361.00 in a phishing scam (Step 5), when the cybercriminal utilizes their stolen information. The potential payout in this scenario results in the cybercriminal netting approximately $1.2 million, with a very low likelihood of detection.
It is important that we remember that when an organization experiences a data breach, the impact on the consumer is far reaching. While it is critical that victims of a breach monitor their financial accounts for abuses as a result of a breach, it is equally important that they take proactive steps to minimize their exposure for residual losses of personally identifiable information that may have been compromised. Understanding the ubiquity of key pieces of information you provide to third parties will help you protect yourself in the event your information is part of a data breach.

No comments:
Post a Comment